Monday 17 February 2020
Eccouncil 312-50 Questions Answers
A. Management buy-in
B. Threat statement
C. Security architecture
D. Impact analysis
Answer: C
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
A. Results matching all words in the query
B. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
C. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting
D. Results for matches on target.com and Marketing.target.com that include the word “accounting”
Answer: B
Tuesday 1 October 2019
Eccouncil 312-50 Questions Answers
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
Expires: Tue, 17 Jan 2011 01:41:33 GMT
Date: Mon, 16 Jan 2011 01:41:33 GMT
Content-Type: text/html
Accept-Ranges: bytes
Last-Modified: Wed, 28 Dec 2010 15:32:21 GMT
ETag: "b0aac0542e25c31:89d"
Content-Length: 7369
Which of the following is an example of what the engineer performed?
A. Cross-site scripting
B. Banner grabbing
C. SQL injection
D. Whois database query
Answer: B
An NMAP scan of a server shows port 69 is open. What risk could this pose?
A. Unauthenticated access
B. Weak SSL version
C. Cleartext login
D. Web portal data leak
Answer: A
Thursday 27 December 2018
Eccouncil 312-50 Questions Answers
A. Information reporting
B. Vulnerability assessment
C. Active information gathering
D. Passive information gathering
Answer: D
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
Time:Mar 13 17:30:15 Port:20 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:17 Port:21 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:19 Port:22 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:21 Port:23 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:22 Port:25 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:23 Port:80 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
Time:Mar 13 17:30:30 Port:443 Source:192.168.1.103 Destination:192.168.1.106 Protocol:TCP
What type of activity has been logged?
A. Port scan targeting 192.168.1.103
B. Teardrop attack targeting 192.168.1.106
C. Denial of service attack targeting 192.168.1.103
D. Port scan targeting 192.168.1.106
Answer: D
Friday 21 December 2018
Eccouncil 312-50 Question Answer
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
Answer: A
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A. WHOIS
B. IANA
C. CAPTCHA
D. IETF
Answer: A
Sunday 5 August 2018
Eccouncil 312-50 Question Answer
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
A. The host is likely a Windows machine.
B. The host is likely a Linux machine.
C. The host is likely a router.
D. The host is likely a printer.
Answer: D
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A. Passive
B. Reflective
C. Active
D. Distributive
Answer: C
Monday 26 February 2018
Eccouncil 312-50 Question Answer
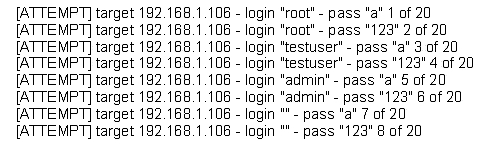
What is most likely taking place?
A. Ping sweep of the 192.168.1.106 network
B. Remote service brute force attempt
C. Port scan of 192.168.1.106
D. Denial of service attack on 192.168.1.106
Answer: B
An NMAP scan of a server shows port 25 is open. What risk could this pose?
A. Open printer sharing
B. Web portal data leak
C. Clear text authentication
D. Active mail relay
Answer: D
Wednesday 27 December 2017
Western Nevada College Receives Grant To Launch Cyber Security Program

More and more corporations, individuals and governments are experiencing cyber attacks around the world. The hackers are breaking the information systems, computer networks, infrastructure and personal computing devices to steal information and personal data for profit.
Anthem, Equifax, Home Depot and Target are just some of the corporations and agencies that have been raped by these hackers in recent years, compromising consumers' social security, driver's license and credit card numbers, as well as other personal information such as birth dates and addresses.
More than ever, there is a need for companies to protect their customers. Consequently, this protection comes from computer and technology students trained in cybersecurity.
Western Nevada College will be able to meet that need in northern Nevada with plans to launch a cybersecurity program.
"As we become more technologically linked, securing and defending critical IT infrastructure becomes paramount," said Dave Riske, CISCO / IS IT / Information Technology instructor at WNC. "The members of the Information Technology Advisory Board of Western Nevada College have identified the need to instill a security mentality in technical employees, Board members have expressed concern for companies throughout Nevada."
Riske has been instrumental in proposing the creation of the program through funding from the Office of Science, Innovation and Technology. The OSIT funding will allow students to acquire more skills and knowledge than they would through seminars.
"The goal of this project is to prepare IT professionals for applied security positions capable of making changes to the environment and IT services of their network," said Riske. "The current training opportunities in the Northern Nevada area for these skills are based on 'bootcamp' training seminars provided by commercial organizations, which are often much more expensive than a university course and are mainly focused in certification and less in the acquisition of skills and knowledge.
"By offering an industry-approved curriculum that certifies the industry recognized by the National Security Agency and the Department of Defense, and meets the training standards of the National Systems Safety Committee, WNC will provide a vital training opportunity for the current IT work force. "
According to the director of the Office of Science, Innovation and Technology of the governor of Nevada, Brian Mitchell, "the need for cybersecurity professionals is growing in Nevada, both in the state government and in the private sector, in Nevada, the rate of growth projected in the number of jobs that require cybersecurity the skills up to 2022 are 30 percent.These jobs have an average salary of around $ 85,000. "
The OSIT grant allows WNC to become an academic training partner of the EC Council, which allows the university to offer certification courses for Certified Network Defender, Certified Ethical Hacker and Computer Hacking Forensics Investigator, expanding the current WNC degree career. The certifications of the EC Council are known and respected throughout the world.
"This makes them an ideal partner, providing reputation, longevity, relevance and relevance in the field of cybersecurity / information assurance," said Riske. "The EC-Council Academic model requires instructors to be certified with each of the certifications offered, in addition to being a Certified Council EC-Council Instructor (or equivalent)."
Students who complete this proposed program will be prepared to work in the industry as specialists in support of computer users, specialists in computer network support and computer repairers, all identified as priority occupations of STEM.
Currently, WNC offers information technology training that provides certification opportunities in the IT industry with Cisco, Microsoft, Comp-TIA, TestOut, Linux Professional Institute and Project Management Institute, many of which are on the credentialing list. Nevada's eligible industry provided by the Office of Workforce Innovation for a New Nevada. These certification opportunities prepare students to demonstrate their competence in numerous technical areas. These existing courses and certification programs will provide the fundamental background to ensure that students are prepared to obtain advanced certifications in CS / IA.
https://wilkescounty.instructure.com/eportfolios/1428/Crestview_School/_Amazon__AWS_Certified_Solutions_Architect__Professional
https://canvas.barker.college/eportfolios/360/Eagle_Mountain_College/CompTIA_SY0601_Exam
https://ccsdschools.instructure.com/eportfolios/1708/Central_Technical_School/HuaweiHCS_Pre_Sale_IVS_Huawei_Certified_Presales_Specialist_IVS
https://atsu.instructure.com/eportfolios/386/Accelerated_Academy/VMwareProfessional_VMware_NSXT_Data_Center
https://ycs.instructure.com/eportfolios/234/Ravenwood_High/AmazonAWS_Certified_Solutions_ArchitectProfessional
https://iebh.instructure.com/eportfolios/732/Foundations_Academy/CompTIA_SY0601
https://umarycontinuinged.instructure.com/eportfolios/2140/Cypress_University/Splunk_Core_Certified_Consultant_SPLK3003
https://sunet.instructure.com/eportfolios/157/Great_Oak_University/CyberArk_Certified_Delivery_Engineer_CAU305_CyberArk_CDE_Recertification
https://canvas.redejuntos.org.br/eportfolios/454/Vivid_Canyon/VMware_1V02120_Associate_VMware_Data_Center_Virtualization
https://educacao.telessaude.ifes.edu.br/eportfolios/5635/Northview_Institute/Network_ApplianceNetApp_Certified_Data_Administrator_ONTAP_Exam
